Proof Of Afterlife By Information
Theorem: If all our past moments still exist within memory, then they will be available to us on the last moment of life. Inside that last moment, consciousness will expand throughout time and space.
Afterlife Information Theorem
1. Memory is Universal, Like Electricity
1.1. On the Universality of Memory
Memory is universal, like electricity - an underlying principle rather than a function limited to brains or machines. Just as electricity flows through wires, storms, and cells alike, memory emerges in biological neurons, digital processors, and even natural systems that record and retain information. It is the persistence of state across time, allowing systems to learn, adapt, and maintain continuity.
Seen this way, memory is not a human invention but a fundamental property of information itself. Molecules "remember" their configurations, ecosystems "remember" patterns of balance, and DNA encodes the history of life. From the firing of synapses to the writing of code, the same universal process unfolds: past inputs shape present outcomes. Like electricity, memory is a common thread linking all domains of science, bridging biology, computation, and physics into one continuous fabric.
1.2. The Memory that AI Uses and that We Use Is Exactly The Same
Proof of Afterlife claims that memory Is fundamental, like electricty. It does not claim the implementations of memory are identical (humans vs. computers), but that memory itself is a fundamental substrate - like electricity or gravity - which both human consciousness and computers are "plugging into."
In that framing:
Human memory isn't just synaptic traces; it's an interface to a deeper informational field (your 4D consciousness).
Computer (AI) memory isn't just weights on a server; it's likewise an interface to that same informational substrate, but through silicon instead of neurons.
Memory as electricity: Different devices (lightbulbs, motors, computers) "use" electricity in different ways, but electricity itself is universal. In Afterlife Theory, memory functions the same way: brains, AIs, and perhaps any conscious system "tap" the same fundamental field.
in Proof of Afterlife view, "fading" memory in life is just an access issue, not a destruction issue - like a device losing power but the grid still being there. [Postulate 1]
Here is a postulate of universality: Memory is not a product of the brain or machine. It is a fundamental property of consciousness itself - an underlying informational field accessible to any system capable of awareness [Postulate 9].
1.3. Memory Manifested in Logic Gates
Memory can be found in many forms and mediums - from the atomic scale to the scale of living systems. But universality does not mean uniformity; instead, it means that memory manifests wherever information is preserved. In human beings, memory takes shape in neural networks; in evolution, it is embedded in DNA; and in machines, it is constructed with logic. Each of these forms demonstrates the same principle: the past is carried forward through a mechanism that retains state. Logic gates, therefore, provide one clear example of how universality can be grounded in engineering, showing us a concrete pathway to build memory into a system.
In the following Section (Section 2), we combine logic gates in particular arrangements - latches, flip-flops, and registers - to construct circuits that can store and recall information. These devices hold a bit of state, preserving input across time until it is intentionally changed. In this way, the abstract universality of memory becomes material: a universal principle expressed through silicon. It is important to note, however, that this is one way to realize memory, not the only way. Nature, biology, and physics offer countless other mechanisms for persistence. Yet by tracing memory down to the level of logic gates, we show not only that memory can be constructed, but that its universality can be systematically demonstrated, reproduced, and understood.
2. Building Memory Using Basic Logic Hardware
2.1. Looking at Memory Addressing
Proof of Afterlife embodeis the concept of perfect memory as a core postulate [Postulate 1]. The basic concept is 'what goes into memory stays in memory.' For the new generation, this is not a hard concept to understand. Computers are engrained into daily life now. We know intuitively that memory does not just drop out. Yet, when it comes to human memory, we have the common consensus that memory evaporates over time. This is because we incorrectly equate our memory with out ability to remember things. Just because you don't remember something, does not mean it is gone forever. On the contrary, the perferct memory postulate states that all memory is retained.
It is hard to believe is how simple memory is to build. It only takes a few basic logic gates to build massive memory. This section is intended to show how simple memory is in terms of underlying hardware. It is not hard to envision how memory could get its start in biology. Being able to save and recall data provides an over whelming edge in terms of natural selection. It may have taken a milliion years, but over time memory was able to get established in humans. Memory is a key component of Proof of Afterlife. Memory capturing space is how the system works. In this section, we take a hard look at the basic hardware of memory. Perhaps biological memory is different, but its functionality is the same. As a programmer, when I envision memory, I see it as a series of mailboxes as shown below. Each mailbox has its unique address. For memory to function, we need to be able to send data from the central processor to the memory location. We also need to retrieve data from the memory location to the central processor. The illustration below shows the computer accessing memory location 0000000010100001.
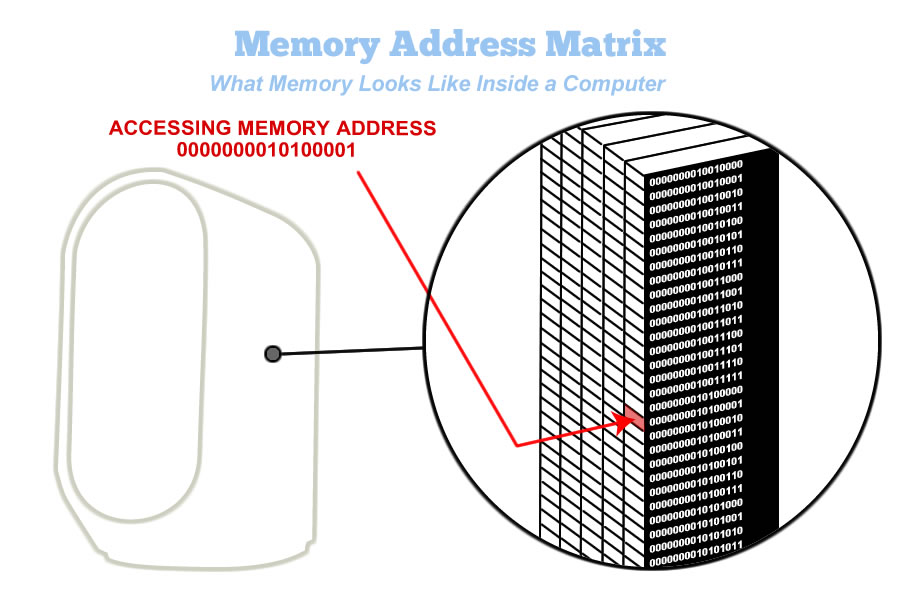
This diagram is a rendition of a single memory location inside a computer.
To make this happen we need to create an Address Bus. An Address bus is a series of wires physically connected to each memory location. An Address Bus is quite simple, being made up of only two basic components: the gate and the not gate. The sections that follow show exactly how to construct a memory bus. We are going to show each basic element, and then conclude by showing how they can be wired together to access any memory location with the computer.
2.2. Foundation of Memory One: The NOT Gate
The NOT Gate is the first basic element of an address bus. Shown below is an electromagnet representation of a NOT gate. The switch, located at position 1 on the left, is the input. Since the switch is open, there is no magnetic pull on the metal switch the switch sits in the closed position as shown on the left. Current is allowed to pass through the switch lighting the bulb on the other side.
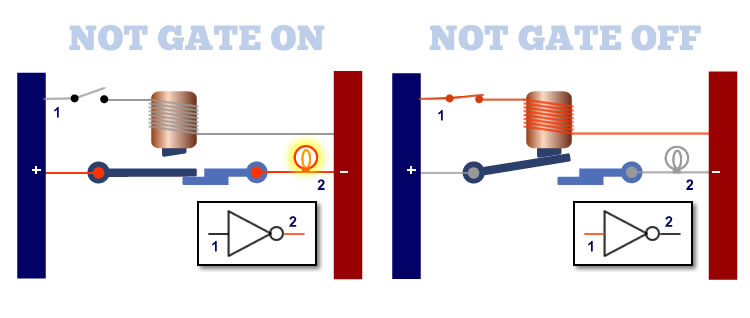
In a NOT gate, when no current is applied to the input, the output is off.
When the input is closed, as shown on the right, the electromagnet becomes energized by applying current to it. The current goes into the coil wrapped around the electro-magnet and pulls the switch into the open position. This breaks the circuit and the light goes out.
The NOT Gate is represented by the symbol in the inset. The NOT Gate functions as follows:
1. When the input is turned ON, the output is turned OFF.
2. When the input is turned OFF, the output is turned ON.
2.3. Foundation of Memory Two: The BUFFER Gate
The buffer gate is the opposite of the NOT gate. On the left, when the input number 1 is closed, the magnet is energized pulling the switch closed. The current flows and the light turns on.
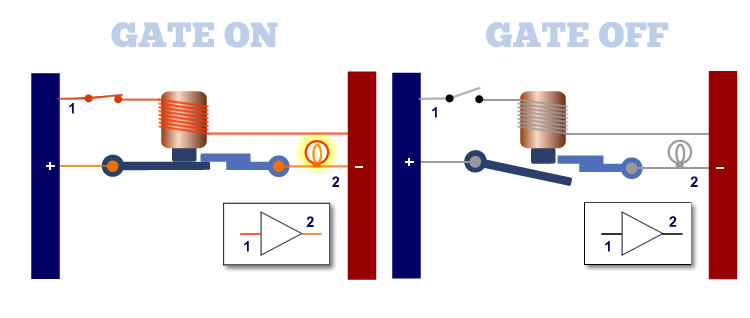
The buffer gate passes the current throug for no net affect. If current is applied to the input, the output is ON.
The BUFFER Gate is represented by the symbol in the inset. The BUFFER Gate functions as follows:
1. When the input is turned ON, the output is turned ON.
2. When the input is turned OFF, the output is turned OFF.
2.4. Components of a Memory Address Bus
A memory address bus contains only two elements: the NOT gate and the BUFFER gate. These components are wired together into continuous memory by an address bus. An address bus is the wiring that gives each specific memory location its unique address. The address bus allows the computer to access one specific memory mailbox from among millions of available mailboxes.
Two basic elements that make up an address bus as shown here:
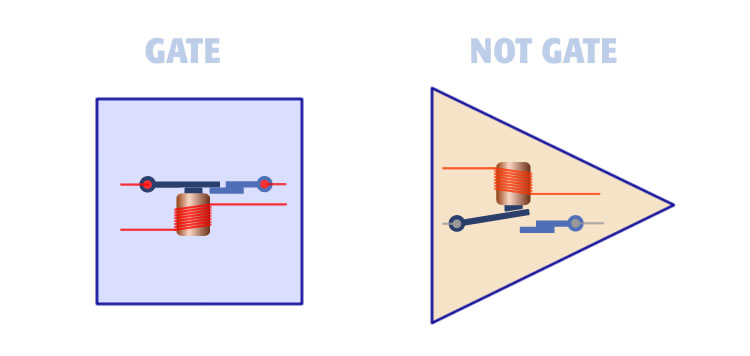
There are only two logic elements in a memory address matrix, the buffer gate and the NOT gate.
1. The first element is the Gate shown left. When power is applied to the input the electromagnet switch is closed and current is allowed to pass. Conversely, when current is no current is applied the electromagnet opens and the current cannot pass. We show this gate is a square.
2. The second element is the NOT Gate. When power is applied to the input of the electromagnet the switch is opened and the current is stopped. Conversely, when no current is applied to the electromagnet the switch closes and current is allowed to pass. We show the NOT Gate as a triangle.
A memory address bus, no matter how large, is made up of just these two elements. The square element opens with the current. The triangle element closes with the current. Creating an address bus is a matter of arranging these two building blocks into a matrix.
2.5. Constructing a Memory Address Bus
The illustration below shows a section of an eight-line memory address bus. The squares and triangles are arranged like binary numbers in a sequence. A square represents a one and a triangle represents zero. Each row of gates represents a unique binary number manifested in hardware.
The top row is eight blue squares. This can be thought of as the memory address 11111111. The second row is 11111110. The third row is 11111101 and so on. The elements are arranged in an array so each row defines a unique number or memory address as shown:
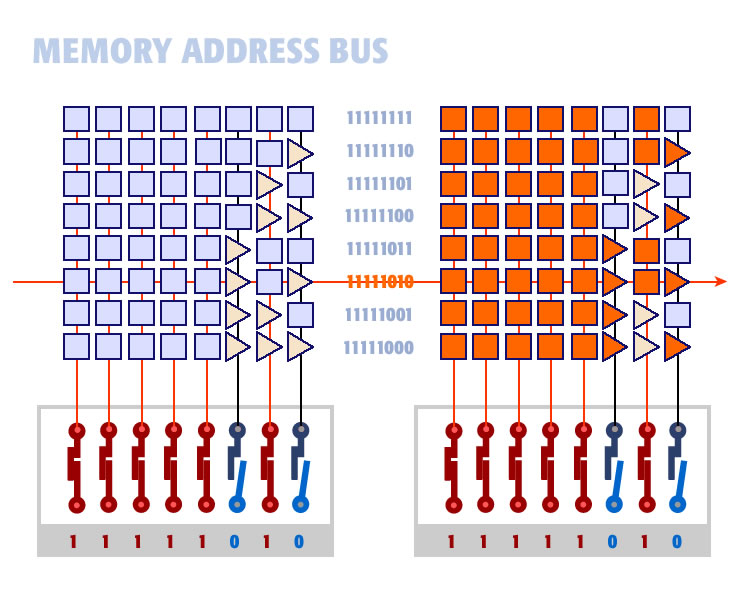
This diagram shows the two memory logic gate arranged in a matrix so each memory location is unique.
We are going to enter a binary number in the address register as shown on the lower left of the diagram above. The number we enter is 11111010. We enter it by opening or closing switches. In this case, we close the first five switches, open the sixth, close the seventh, and open the eighth.
The result is turning ON lines 1 to 5, and 7 and turning OFF lines 6 and 8.
On the right you can see how our memory matrix reacts to the current on the address lines. Those elements that are turned on are shown in orange:
1. All squares turn ON when the current is applied.
2. All triangles turn ON when no current is applied.
As you can see only one memory address matches the binary number entered on the bus. That is memory location 11111010. It is the only combination of squares and triangles that light up, all the way across, allowing current to pass from left to right. The memory bus applies current to that one memory address only.
The arrangement of gates is how computers store and access data to and from unique memory addresses.
The memory address bus shown above is called an eight-bit address bus. That means that this computer has eight data liines running throughout its architecture.. In terms of addressing, this computer can accommodate an eight-bit binary number. That meams this computer has 256 total memory locations. You can see from the illustration above how simple memory is.
Today's computers are 64 bit. That means they have 64 data lines running throughout its architecture. Even though we add more data lines, the basic concept is exactly the same. The addition of every data line, for example from eight data lines to nine, doubles the number of memory locations reachable by the processor. For examle, a 64-bit address space can hold 17,179,869,184 GB (17 billion gigabytes). Memory is simple in concept, but powerful in execution. As lines are added, the number of memory locations goes up exponentially. Today's computers have 64 address lines and can reach an astonishing number of memory addresses, each containing 64 bits of data.
3. Constructing a Memory Binary Digit (BIT)
3.1. Foundation of Memory: Not, And, and Nor Gates
Memory can be created from just three simple, elemental building blocks. Fully functioning memory can be built using only the NOT gate (previous section) and the following two elements: the AND gate and the NOR gate.
3.2. Foundation of Memory One: the And Gate
The AND gate has two inputs as shown on the left.
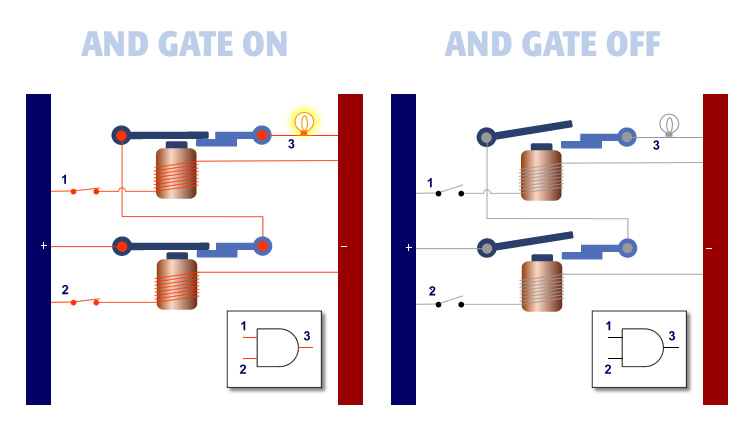
The AND gate has two inputs. When both inputs are ON, the output is ON. When one or both inputs are OFF, the output is OFF.
The AND Gate will allow current to pass and light the bulb when current is applied to both inputs. The AND Gate is easy to remember because it will light the bulb when current is applied to Input 1 AND Input 2.
The AND Gate is represented by the symbol in the inset. The AND Gate operates as follows:
1. When both inputs are ON, the output is ON.
2. When either of the inputs are OFF, the output is OFF
3.3. Foundation of Memory Two: the NOR Gate
The NOR gate has two inputs also. It functions differently than the AND gate. We are showing NOR in the example below so you can see exactly how it operates.
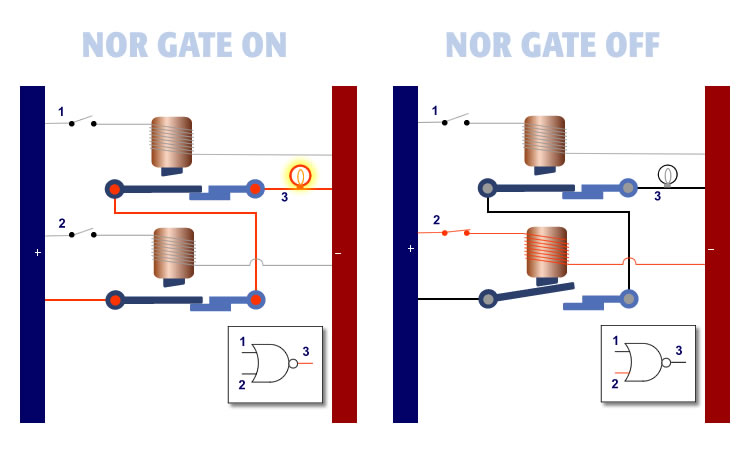
The NOR gate is the opposite of the AND gate. When both inputs are OFF, the output is ON. In all other cases, the output is ON.
On the left, no current is applied to either Input 1 or 2. With no current applied, current passes through the NOR Gate and lights the bulb.
On the right, current is applied to Input 2, the lower electromagnet. This opens the lower switch. The current is no longer allowed to pass through the first gate. The current applied to either input will stop current from going through this device. The NOR Gate is slightly harder to understand than the other gates. This is because it turns ON when there is no input and OFF when there is input.
The NOR Gate operates as follows:
1. When both inputs are OFF, the output is ON.:
2. When either input is ON, the output is OFF.:
3. When both inputs are ON, the output is OFF.
3.4. Bringing Memory to Life with a Flip Flop
A Flip Flop is a common device used in memory where two NOR gates are wired together as shown below. When NOR gates are arranged this way, an amazing thing happens. The simple electrical device gains the ability to change states permanently via momentary electrical impulses. It is like a switch that can be turned on or off by electricity. Once a flip flop is set to a state, say off, it will remain in the off state until it is sent another electrical impulse. That makes the flip-flop a perfect device for storing data. Once set, it will stay in either the ON or OFF state indefinitely.
A flip-flop is two NOR Gates combined in an arrangement as shown below. The output of one gate is connected to the input of the other gate and vice versa:
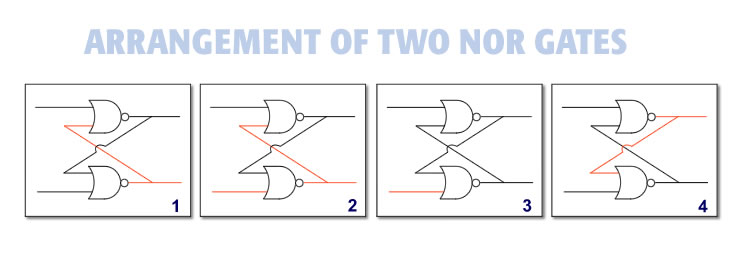
A flipflop is a small device made by wiring two NOR gates together as shown. A flip-flop can be set permanently with a single burst of electricity.
Figure 1 shows the flip flop in state one, where the top output is OFF. Consider this system at rest. With no current applied to either input on the bottom NOR Gate, the output is turned ON. This cuts off the current to the upper NOR Gate. The flip-flop will remain in this state indefinitely barring outside influence.
Figure 2 shows the current being applied to the lower input of the bottom NOR gate.
Figure 3 shows the output of the lower NOR gate turning OFF due to the current applied to one of its inputs.
Figure 4 shows the output of the upper NOR gate has turned ON due to no current applied to either input. Consequently, current is applied to the lower NOR gate. This locks in the state by keeping it turned OFF. Now the flip-flop is set to a second state where the upper NOR gate output is ON. It will stay that way and is at rest.
The flip-flop is an amazing piece of hardware. This simple arrangement of two NOR gates allows this device to have two states. It can be either ON or OFF. If the flipflip is in the OFF state, current applied to its input will cause it to 'flip' to the ON state. It will stay in the ON state indefinitely. Then you can apply current to the flipflop in the ON state, and it will 'flop' to the OFF state. This way we can apply a momentary burst of electricity to SET the flipflop in one of two states. This makes it the perfect electronic device to store information. For example, if we want to SET a binary number into 16 flipflops, we merely need it hit each one with a momentary burst of electricity and the number becomes permanently set into the series of flipflips. We just hit them one time and the state becomes permanently set into the hardware.
At the center of each memory location is a flipflow. For example, if you have 16 flip flops you can store a 16-digit binary number. Merely set the digit 1 to state one and 0 to state two. When you set a number into the 16 flip-flops, that number will remain there indefinitely. This arrangement is duplicated millions of times in a computer. It is a simple basic device repeated millions of times.
The flip-flop forms the foundation for memory. Given enough flip-flops we can store unlimited data. A flip-flop is a foolproof way to store information in hardware.
3.5. Storing the ON and OFF state into a Bit
A BIT is short for binary digit. It is the smallest piece of computer memory. It is capable of storing a single binary number, either zero or one. A computer bit is a flip-flop wrapped in a few basic circuits. The flip flop is the hardware mechanism that stores the data. The illustration below shows how a bit is set with data input and a clock:
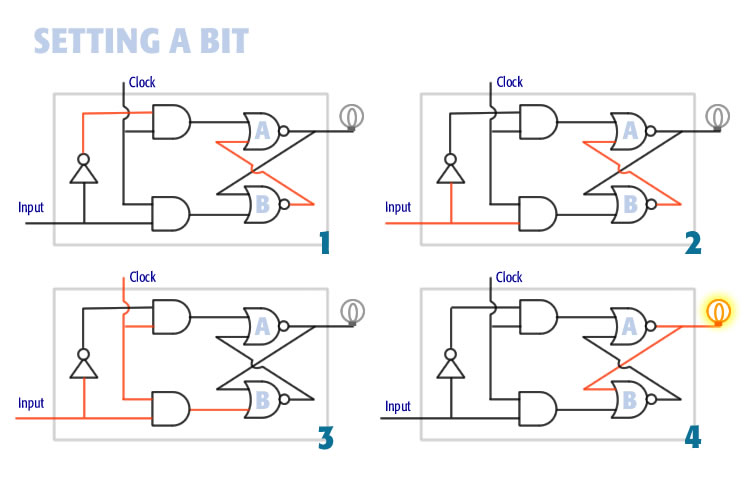
This diagram shows a single memory bit. In frame one, the bit is OFF. In frame 2, current is applied to the input. In frame 3, the clock goes high. In frame 4, the bit is permanently set to ON.
Figure 1 shows the bit at rest in the OFF state, indicated by the light being off. NOR Gate B is ON because there is no current on either input.
Figure 2 shows the input line turning ON. The input line comes from the memory address bus indicating that this memory location is being worked up.
Figure 3 shows the clock line turning ON. Note that both inputs on the lower AND gate are turned ON. Since both leads are ON, current passes through the AND gate into the lower NOR gate B. Since an input line of NOR Gate B is on, it turns device B OFF.
Figure 4 Since both leads into NOR Gate A are OFF, the device turns ON. This lights the bulb and the bit is at rest in the ON state.
3.6. Diagram of a Complete Memory Bit
This illustration below shows a full implementation of a computer bit. It shows the addition of an address line and a read/write line:
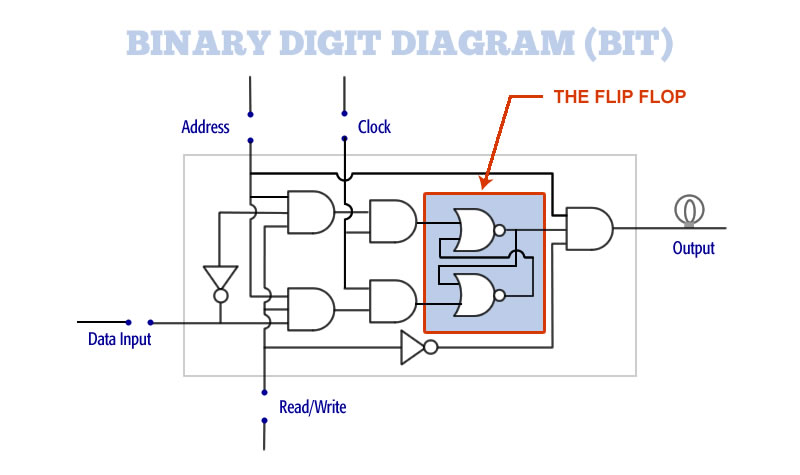
This is a diagram showing a complete memory bit, including data lines, address lines, clock, read-write, and output. At the heart of the memory bit is the flip-flop.
This is a computer bit. Here is how it works:
To Write Data (shown left):
1. Turn the address line ON
2. Turn the read/write line ON
3. Turn the clock line ON
4. Enter your information on the data line (ON for one, OFF for zero)
The illustration on the left shows the address line ON, read/write line ON, and data line ON. These AND together. The input state (ON or OFF) gets through to the second AND gate where it is ANDED with the clock line. When the clock line is ON the data sets into the bit.
3.7. Fully Functioning Memory Matrix
Memory bits are the same bit hardware repeated thousands of times arranged into a matrix. The illustration below shows 16 bits arranged into a four-by-four memory matrix. Each bit is identical. The illustration shows how bits are connected via the address bus, data, read/write, clock, and output lines.
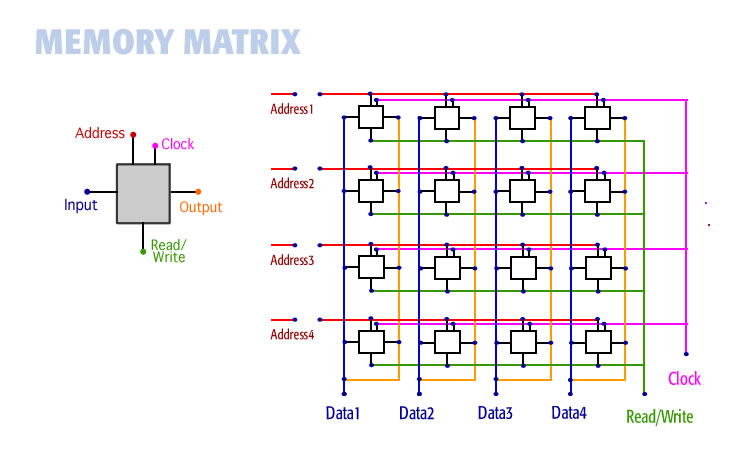
This is a diagram of a memory bus within a computer. It shows 16 memory bits, arranged into a matrix, with the wires required to set and unset the bits.
Reading data is a matter of turning ON or OFF the various lines. For example, the read/write line tells the computer whether you are reading data from a bit or writing data to it. This 16-bit memory shown above is accurate. Memory in a computer is like this but there are more bits.
3.8. Three Concepts about Memory That Will Eventually Be Proven Medically
Concept 1: Human Memory Drops Just One Bit - At the Last Moment of Life
We went through this exercise of building memory to show how it works in a computer. Is human memory the same? Obviously no, but it functions the same. Computer memory uses transistors to store and retrieve data. Human memory uses nerves. While the underlying hardware differs, the basic functionality of memory is the same.
Building computer memory above we can see how simple and reliable it is. But how can we see how memory works in humans? Very easily. All we need to do is look around us. The environment you are in now is already in memory when you experience it. That fact gives rise to a whole new way of thinking about memory. You can think of our memory as a long tube stretching back far into the past. Currently, we sit at the very leading edge of that tube. We are in the present, at the leading edge of memory. Put another way, your surrounding environment is memory.
The ultimate test of this "environment as memory" concept is to move awareness from the present to some point in the past. This would be time travel. If you could do this, you would find that the memory of the past exists, exactly like it was when you experienced it the first time. While we can't do it, we can theorize it. And if we could, we would find the past moment is still there, intact. [Postulate 2]
We often hear that when people are near death they experience a life in review. During these times people see their past moments in great detail. Medical science does not take these accounts as seriously as they should. We tend to be misled by the act of remembering. Remembering distorts the true nature of memory. It makes memory seem fragmented, like it is full of holes. That simply is not true. Memory is complete and total. It is our ability to remember that is limited. Memory is unlimited. It starts here, at the moment of the present which is the leading edge of memory. It extends back in time, unbroken and perfect, all the way to the beginning. Nothing is lost, ever. That is how to understand the true concept of human memory.
Concept 2: There is a Finite Upper Limit to Life Expectancy
Memory needs to be looked at as the accumulation of all moments of life [Postulate 4]. Each moment gets absorbed into memory as it happens and it gets retained there. Each moment requires an amount of memory to retain it. As the moments in one's life accumulate, memory gets used up. This goes back to the concept of perfect memory. Reality gets absorbed into memory where it is retained forever. If we live long enough, eventually we will run out of memory. It looks like this upper limit is about 120 years. The idea that we can live forever cannot happen because we will eventually run out of memory. Since memory does not drop bits, sooner or later it will become full.
Concept 3: End Of Life Is Caused by Data Disruption, Not Physical Trauma
Back in the early days of programming, there was a phenomenon in the Windows operating system called the blue screen of death. You would be using your computer, and then all of a sudden the system would break and you would get a blue screen. What happened was the computer lost its place in memory. The system broke. It didn't know where it was. It was a memory fault. It caused the computer to die immediately and without warning. It died right on the spot.
The end of life in humans happens much the same way. It is a data thing, not a physical thing. It looks like physical trauma, such as sickness, causes the end of life. If physical trauma brings about dropped data it causes end of life. If it doesn't, life goes on. The end of life is much like the blue screen. It is brought about by losing data.
When something occurs in memory so the memory is not intact (a single dropped bit), life stops at that moment. It blue screens. It is memory dropping a bit that causes the end of life. This happens immediately. When the first bit of a lifetime is dropped, life stops and the end of life ensues. The first dropped bit must cause the end of life because every moment, from concept to the present, is perfect. It must be that way because during life we are building a universe in memory. That universe will be there at the last moment of life. This is life's grand design.
4. The Central Processing Unit (CPU) - The Center of a Computer
4.1. Overview of a Miracle Computer Processor
The CPU (Central Processing Unit) serves as the "brain" of a computer and plays a pivotal role in the "miracle" of data storage and retrieval. Here's how it orchestrates this complex yet seamless process:
1. Processing Instructions: When you request to store or retrieve data, the CPU processes the necessary instructions from software or the operating system. It interprets these instructions in its instruction set, breaking them into a sequence of operations. The illustration below shows the exterior of a processor. The processor has 16 address lines (shown in red) and 16 data lines (shown in blue). It also has a read/write line (shown in green) and a clock line. This processor is intended to work with 16-bit memory as shown on the left. 16-bit memory has 16 address lines and 16 data lines. We wire our processor on the right to the memory on the left. Now we have a computer.
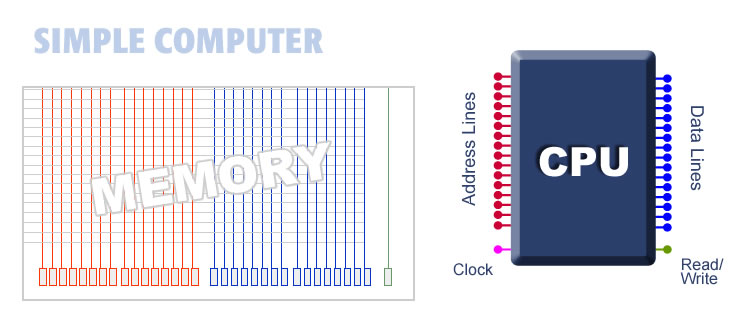
Artist rendition of a computer with 16 data lines, 16 address lines, a clock liine, and a read/write line
2. Managing Memory: The CPU interacts with RAM (Random Access Memory) to temporarily store data that is being actively used or processed. It ensures fast access to data by keeping frequently used information in cache memory, reducing latency and speeding up operations. For long-term storage, the CPU sends and retrieves data to and from devices like hard drives, SSDs, or external storage through specialized controllers.
3. Error Checking and Validation: The CPU ensures data integrity by using error-checking mechanisms during transfers, like parity bits or checksum validations. This guarantees the data retrieved matches what was stored.
Through these steps, the CPU seamlessly integrates complex operations, enabling us to store and retrieve massive amounts of data almost instantly. This interplay of logic and mechanics is what makes the process feel miraculous to us.
4.2. Retrieving Data from Memory
Our small 16-bit computer contains 65,000 memory locations. That is 2 to the 16th power. That is how many memory locations 16 address lines will support. Each memory location has 16 bits of data. The total number of bits our processor can support is 65,000 multiplied by 16 or 1,040,000 bits. With memory connected to the processor, it can access any bit within its memory. Our processor's 16-bit wide architecture allows us to place a memory address in a data register and reach any location in memory.
Reading data from a memory location, into the processor, is done in three steps:
1. Load a memory address of the data location to be read into data register A.
2. Execute the read memory instruction.
3. The contents of the memory location currently in register gets copied into register B.
The information is read into the processor immediately as shown here:
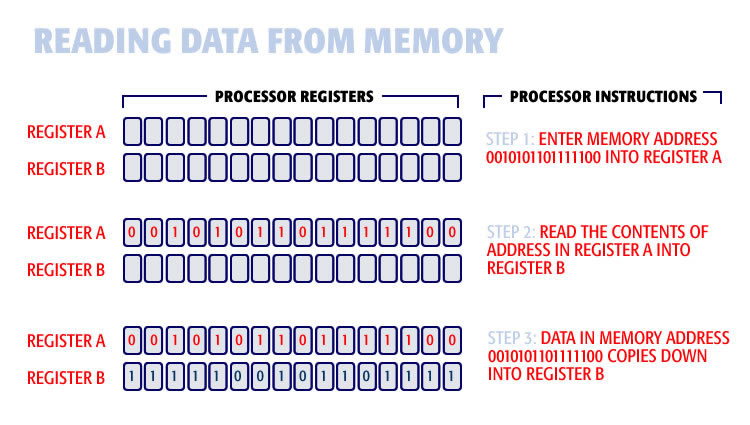
These are the memory registers inside the processor. To read data from memory, we load the memory address register A, issue the read instruction, and the data is brought down from memory into register B.
4.3. Storing Data into Memory
Writing data from the processor to memory is a three-step process:
1. Move the memory address of the location to be read into data register A.
2. Move the data to be written into data register B.
3. Execute the Write Data instruction.
Writing data happens immediately. The data will overwrite whatever is in the affected memory location.
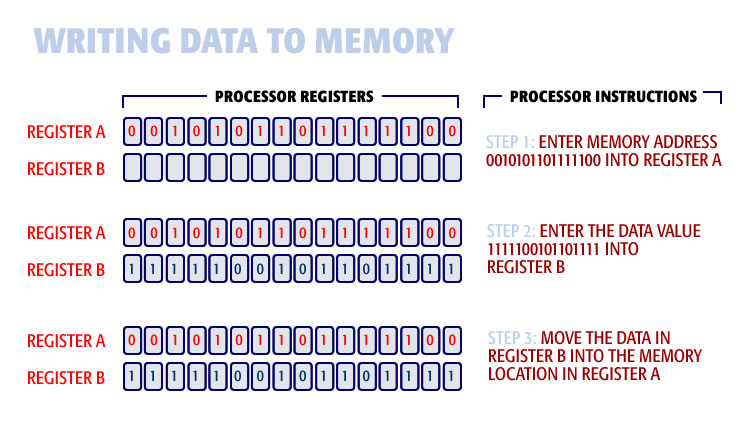
Writing a data-word, from a register in the processor, to a remote memory location, is to load the data into one register, load the address into a second register, then issue the write command.
4.4. Human Thought as a Running Computer Program
The concept of human thought as a running computer program likens the mind to a dynamic, self-adaptive system of information processing. In this analogy, the brain serves as the hardware, while thoughts, emotions, and cognitive processes function as the software. Just as a program executes instructions based on inputs, human thought processes sensory information, retrieves memories, and applies learned patterns to generate decisions and responses.
A computer "thinks" by loading computer instructions into the processor and executing them. Once the processor has finished executing one instruction, it loads the next instruction and executes it. Each new instruction is loaded into the processor on each cycle of the clock. The computer operates like a machine by executing one instruction at a time as the clock line turns ON and OFF. The clock keeps everything in order.
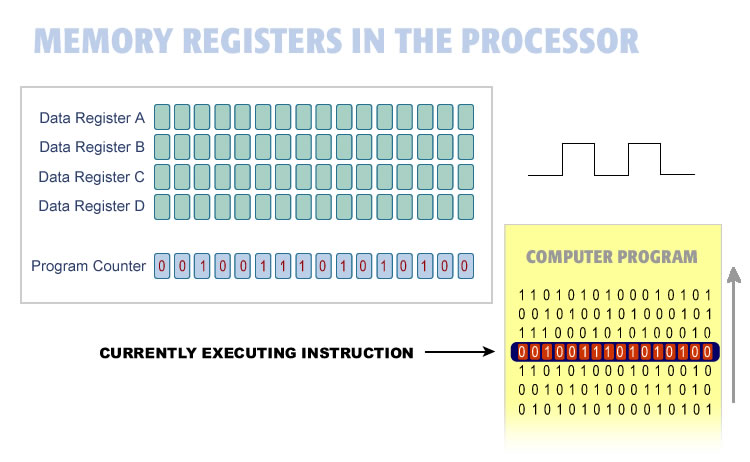
A computer program (shown in yellow) is a list of memory locations, data to be worked on, and processor instructions into a single program. The program runs by executing each line in succession.
This illustration shows a simplified processor, with four data registers and a program counter. When the program counter increments, it moves the next program instruction into the processor and then executes that current instruction.
Every processor has an instruction set. The instructions set is a collection of instructions that the processor can execute. Each instruction does one specific thing such as adding two numbers together. The instruction set is limited to instructions like adding, moving, or manipulating data. Each processor instruction does very little but in combination the instructions form a powerful programming language.
The processor executes each instruction one at a time as follows:
1. The program counter increments one.
2. A new instruction is loaded into the processor with the next beat of the clock.
3. The instruction is executed.
4. The processor acts upon the data in its registers as dictated by the instruction.
5. Go to step one.
While a computer is capable of fantastic things, during any one moment it is only doing one very specific thing. It only executes one instruction at a time. Each computer instruction involves movement or manipulation of data. The processing takes place within the processor's registers. The processor moves data from memory into its registers. However, the manipulation and control of data take place within the processor. The computer moves data from memory to the processor, operates on it, and moves it back to memory.
The computer is "aware" of what is happening to the data inside its processor. The processor is surrounded by memory. However, data operations take place inside the processor. The difference between at-large memory and data register memory inside the processor is that data registers are operated on and are under the direct control of the processor. It is the execution of instructions that manipulate data within the processor that characterizes awareness. The computer is aware of the movement and manipulation of data within its processor.
4.5. Likening an Executing Program to a Train of Thought
As a programmer you must learn to read your program. Imagine you have completed programming for the day. Then you come back the next day. You open your program and read it. You read your program by putting yourself in the perspective of the processor. In other words, you start at the top of the program looking at the first line, and then mentally execute it. Then you go to the next line, exactly like the processor would do. Then you mentally execute that line. Then you go to the third line, and so on. If you are a good programmer and if your program is well written, you can follow the logic (the processor's path) from the first line to the last line, mentally interpreting each line as you go. If you can do that, you know what the program will do next.
Shown below is a sample computer program. Open your program and look at the first line. That is your initial point of focus. Like the processor, take in one line and mentally execute it to find out what it will do. The entire program may be thousands of lines long, but your focus at this moment is on the first line. You read a program by moving that point of focus down the page one line at a time. The red lines show how the processor moves from line to line through a computer program.
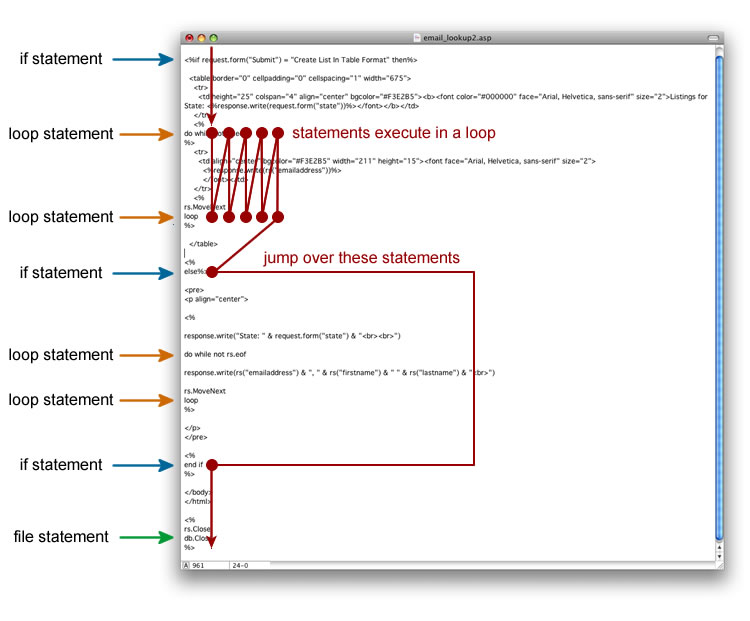
This is a diagram that follows the processor activity as it executes the program. The red line shows how the processor executes the program one line at a time.
At times during the program you may enter a loop as shown above. During this time your point of focus starts at the first line of the loop. You mentally execute each line of the loop and then jump back to the top of the loop, as the processor would do. In the example above the program is reading email addresses from a database and printing the results to a table on the screen. Your point of focus may jump around physically in the program. Program execution jumps several lines after encountering an if statement. However, the logic - the processor path through the program - remains the same. You mentally execute one instruction at a time from the first line of the program to the last.
Awareness operates like the focus within this program. Like the red line moving through the program, our awareness moves within the environment. Awareness acts like program execution within this program. Awareness, like program execution, is located in one place at a time.
At no time when reading a computer program do you mentally execute two instructions at once. Program execution happens sequentially. You look at one instruction and figure it out. Then you look at the next instruction and figure that out. This is also how awareness works. You focus on one thing and acknowledge it. Then you focus on the next thing and acknowledge that. As the processor interprets each instruction of a program sequentially - awareness acknowledges each thing sequentially. Awareness within the environment works like a focus within a program. That is why thinking is called a line of thought. That is why awareness is called a point of view.
5. Comparing Computer Memory to a Human Environment
5.1. Viewing Reality as Surrounding Memory
Memory absorbs the environment as we move through life [Postulate 2]. The environment is made up of visual, sound, and other sensory stimuli, as well as any thought going on. The present moment is like the memory space of a computer. The environment is absorbed into memory. As each moment happens, it passes into memory. Essentially memory stores reality. Reality gets filed away in memory as we experience it. Here is a representation of the human mind and the computer model:
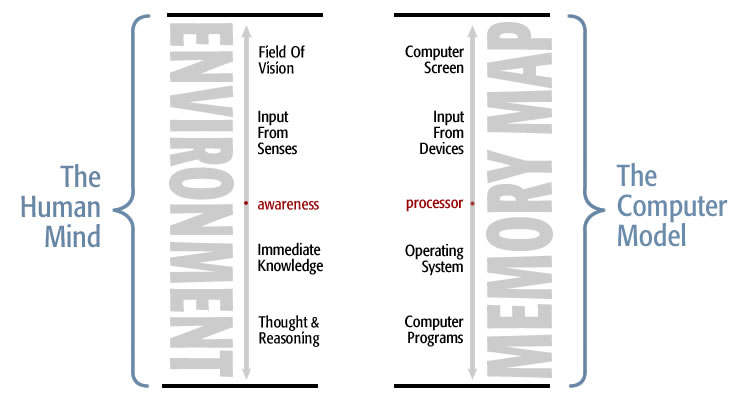
This illustration compares the surrounding environment with the memory map of a computer. Both are rendered in memory.
The Human Mind and The Computer Model are similar. Both are based on memory. Both have a processor that acts as the center of their universe. Both include everything that is going on at the moment.
5.2. Could a Computer Store Reality?
Awareness is like a processor running a program. The environment is like random access memory surrounding the processor. Memory is like random access memory (RAM) containing everything going on inside the computer at that moment.
Random access memory (RAM) contains everything; the operating system, data input, and running applications. Likewise, our memory in the present contains everything; the physical world, any thought going on, and any input being absorbed. Here is a diagram of our random access memory at the present moment:
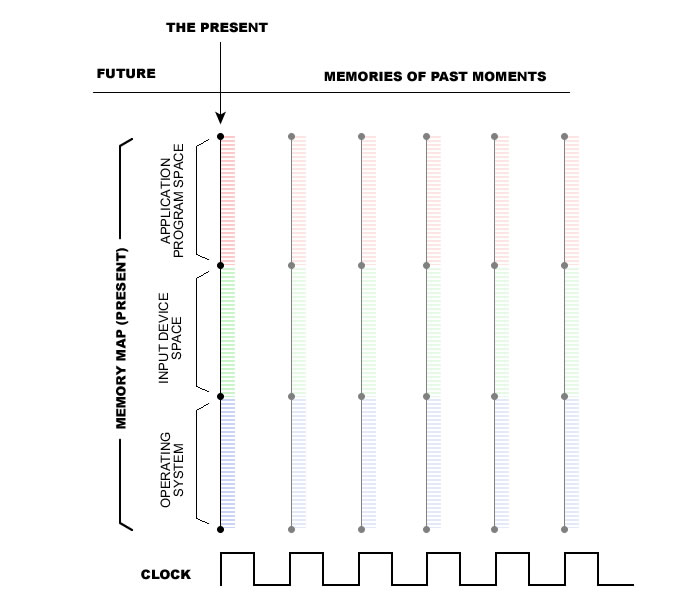
This is a side-view of the memory map of a computer. Each vertical line represents all the memory in the computer at that point in time.
Computers have an internal clock. The internal clock sets a cadence for the computer by turning the clock line off and on. Inside a computer, time is not continuous. Time is made up of beats or pulses. Instructions of a computer program are executed when the clock line is ON.
The illustration above shows how the entire memory map of a computer could be read into memory each time the clock line turns ON. The entire memory map is copied onto memory on each beat of the clock. A system like this could save all realities from the beginning to the present. A system like this would save its memory space continuously as it unfolds.
5.3. How Memory Stores Three-Dimensional Space
Perfect memory stores three-dimensional space perfectly. We have seen how reality gets absorbed into the visual cortex. As we move through life, we are constantly absorbing perfect copies of our current environment into memory. Using memory, we absorb each three-dimensional space as we experience it. It happens in the background. We are unaware that this is happening. That is how we experience the surrounding environment as shown below:
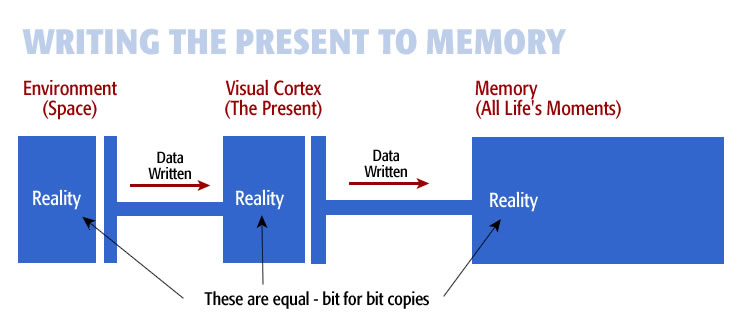
This diagram shows how the mind processes the environment into memory. Reality begins on the left, is built in the visual cortex, and is saved in long-term memory on the right.
Think of your memory as reaching out to absorb the present. The present - the outside world - is within memory. We live within memory always, even in the present.
The present environment appears real to us. The rest of memory is just as real too in the same way. Moments get absorbed into memory as we move through life. Awareness stays in the present moment. Just because awareness is not currently located in memories of the past does not mean that the memories of the past are not complete, vivid, and pristine in every way. The memories of the past are just as real and complete as the present moment. We simply cannot realize past moments fully right now because our awareness is no longer in that moment. It is in the present.
If we could theoretically move awareness from the present to a moment of the past, we would experience that past moment exactly like we experience the present moment. That moment of the past still exists. It has not gone anywhere. We just cannot recreate it at this time. That does not mean that we never will. It is enough to say that all those past moments exist, waiting to be fully realized.
5.4. The Memory Requirements for Storing Moments Indefinately
If your mind is going to capture and retain all moments throughout your lifetime, you are going to need perfect memory. Is it possible for human memory to achieve this level of perfection? For this to be possible we need a memory device that can hold every moment you have ever experienced throughout your lifetime. These moments are complete realities including any thought going on at the time. We need to store them completely without dropping even one bit. We are talking about a perfect, bit-for-bit storing of your entire lifetime.
This is a lofty ideal. It does not seem possible. Everyone knows that cells do live indefinitely. There is a turnover of the memory hardware within the brain. It does not seem realistic that the brain can make it through 120 years of life without ever dropping a bit. It would seem that the underlying hardware would eventually fail and lose the data that was stored in that hardware. However, it is possible to maintain perfect memory even when the underlying hardware fails. Maintaining perfect memory using imperfect hardware is what we will look at next.
6. Accumulated Memory as a Realm of Space and Time
6.1. Massive Increase of Memory Capacity by Adding Data Lines
Most tend to think that doubling the number of data lines in a computer magically doubles their power. They proudly proclaim, "Hey, my new 64-bit machine is twice as powerful as the 32-bit beauty I used to own." But hold on a sec, that's not quite how memory works.
When you add those data lines, you are doubling computer power with each line. So, a 64-bit machine has taken a huge leap of power, doubling a total of 32 consecutive times! That's right, 32 times!
Computer power is all about that memory space, that vast arena where your computer can roam and crunch those numbers. As the memory space expands, your machine gains more room to flex its computational muscles. It is not simply a doubling of raw power. Oh no, it is monumental memory expansion!
Here is what that progression of data lines and exponential expansion of memory looks like:
2 data lines yield 4 memory locations
3 lines yield 8 locations
4 lines yield 16 locations
5 lines yield 32 locations
6 lines yield 64 locations
7 lines yield 128 locations
8 lines yield 256 locations
Each additional data line doubles addressable memory. As lines are added, addressable memory skyrockets at an accelerating pace. Memory growth is exponential as shown here:
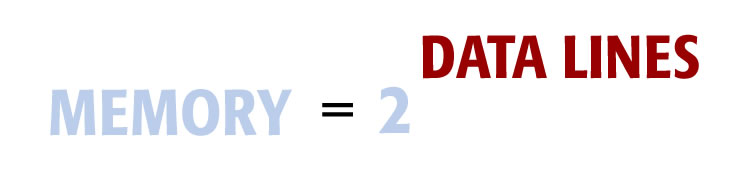
This equation shows the relationship between memory and the number of data-lines in a computer. If the computer has eight data lines, the total memory is 2 to the eighth power, or 256 memory locations.
This equation is read as follows: Memory capacity is equal to two to the power of the number of data lines.
6.2. The Impressive Capacity of 64-Bit Memory
Let's dive into the mind-boggling memory capacity of a 64-bit computer. It's like stepping into a sci-fi dream come true! Just imagine this 64-bit machine, with its CPU registers, address lines, and memory locations all strutting a cool 64-bit wide. It's like an orchestra of bits, playing in perfect harmony!
Now, here's where the magic happens - with 64 data lines running throughout its memory, connecting every little piece of hardware like a puzzle. It's like a symphony, with each instrument playing its part flawlessly.
Hold on because we're about to reach the stratosphere of memory addresses! Brace yourself for this mind-numbing fact - a 64-bit processor can soar up to 2 to the 64th power, that's 18446744073709551616 unique memory addresses! Whoa, that's more than 18 quintillion! I can't even fathom that number.
With a 64-bit memory address, this processor can directly access 2 to the 64th power of addressable memory locations, each holding 64 bits of data. It's like a treasure trove of information, waiting to be unlocked and realized! Having that much raw memory capacity at your fingertips, it's like embarking on a thrilling journey into a universe of limitless addressable memory!

This equations shows the number of memory locations in a computer with 64 data lines. The result is 64 squared, which is 18,446,744,073,709,551,616 memory locations.
See that equation above? That is the size of memory we're talking about for a processor 64-bit wide. Don't let that number scare you - 18,446,744,073,709,551,616. It's one heck of a LARGE number, no doubt about it.
Here's the kicker - you only need 64 data lines to handle all that memory! That is like a perfectly efficient setup. Given the physical size of our brain, it is large enough to handle that 64-bit processor with all that memory. Imagine the possibilities! We could store realities, one after another, in that gargantuan memory space, and still have room for more!
Let your imagination run wild. With this capacity of memory at our fingertips, we can store a whole bunch of realities before we even start to think about running out of memory.
6.3. The Relationship of Aware Memory Versus Unaware Memory
A data word is the size of the registers in a processor in bits. The size of a data word equals the number of data lines in the computer. In a 64-bit computer, a data word is 64-bit long. The data word is also the size of each memory location. In a 64-bit computer, each memory location contains 64 bits of information. In a computer, the memory (in the processor) being driectly acted upon is said to be aware memory. All other memory, not being acted upon, is said to be unaware memory. This equation expresses the relationship between aware memory (inside the processor) and surrounding unaware memory.
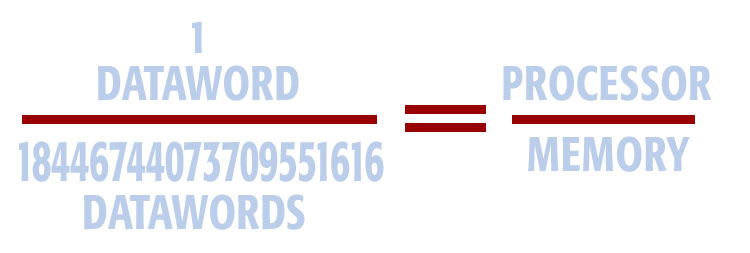
In this diagram, we compare one data-word (processor register) to total memory in a 64-bit computer. The result is one over 17 billion.
Thought, in a human, is analogous to data movement in a processor. A computer will load data into the registers of the processor and then act on that data. It may be moving a 64-bit data word into a register, a 64-bit memory address into another register, and then moving that data from the processor register to that memory location on a single cycle.
During that cycle the computer acts on those registers inside the processor. In a sense, the computer is aware of the data it is acting upon. The relationship between the data being acted upon versus all other data in the computer is expressed above.
6.4. Comparing Memory and Processor to Memory and Awareness
The memory/processor relationship in computers provides an accurate model for the memory/awareness model in humans. Computers, at any one moment, focus on an infinitesimally small amount of data. Yet it is surrounded by a large environment of memory. The computer focus takes place on a single clock cycle.
Humans focus on a single moment too. It is called the present. The computer model assists us in seeing this relationship between awareness and memory. Without the computer model, we would overestimate the information we are aware of at any one time. We also underestimate the information making up the surrounding environment.
The true relationship between awareness (information we focus on) and the surrounding environment (memory) is the same as a computer. That relationship looks like this:
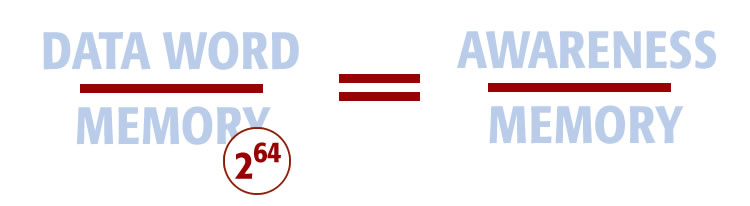
In this equation we make a direct comparison between a data-word over total memory, and conscious awareness over memory (environment).
A 64-bit computer yields astronomically large memory using a data word that is infinitesimally small in comparison. A 64-bit computer is used for illustration purposes. I have no idea of the size of the data word in the human mind, or even if it is binary. However, the relationship between the data under direct processor control and its surrounding memory holds for both computers and humans.
6.5. Is it Possible to Store a Lifetime In Memory?
Let us delve into the intricacies of human memory. In the fabric of our being, memory absorbs each surrounding environment as it unfurls its tapestry before us.
Oh, the marvels of human memory. Memory reaches back and grasps the threads of all moments throughout our lifetime. A grand archive it becomes, storing experiences and knowledge, layer upon layer, woven intricately within the depths of our memory.
Now, let us turn our gaze towards the question that beckons our inquiry: How much memory is required to store the entirety of this life-long repository? The sheer magnitude of such a task would confound even the most brilliant minds of our age. To unravel this enigma, we must fathom the vastness of human experience and the limitless horizons of time. The encounters with loved ones, the triumphs and tribulations, the sights and sounds that color our days - all have their place in this boundless expanse of our memory.
Yet, to quantify this immense reservoir is a task that we can only approximate, for it resides within the ethereal realm of our consciousness. It transcends numbers and calculations. The measure of human memory dwells in the immeasurable realms of the soul. That said, let us embrace the wonder of human memory where the echoes of our existence reverberate through time. Using simple mathematics, let's attempt to unlock the mysteries of our memory and marvel at the miracles it holds.
First, let's calculate the number of seconds in 100 years. That is pretty much the upper limit for life duration, give or take. It turns out there are 3,155,673,600 seconds in 100 years.
Next, let's calculate the number of memory locations in 64-bit memory. There are 18,446,744,100,000,000,000 memory locations in 64-bit memory.
Now we are going to divide the total memory locations by the number of seconds in 100 years. There are 5,704,011,970 memory locations available to store each second of life, given a lifespan of over 100 years.
Since this is 64-bit memory, each memory location can store 64 bits of data, or 8 bytes.
That means there are 45,632,095,760 bytes of new memory available to absorb each second of life.
One gigabyte is equal to 1,000,000,000 bytes.
That means there are 45.6320958 Gigabytes of memory available to record each second of life, over a 100-year lifespan.
Now let's look at the three-dimensional model we used in the evidence/virtual reality section. The model includes the house, the yard, all interior rooms, and furnishings. It is a fully detailed environment as shown here:
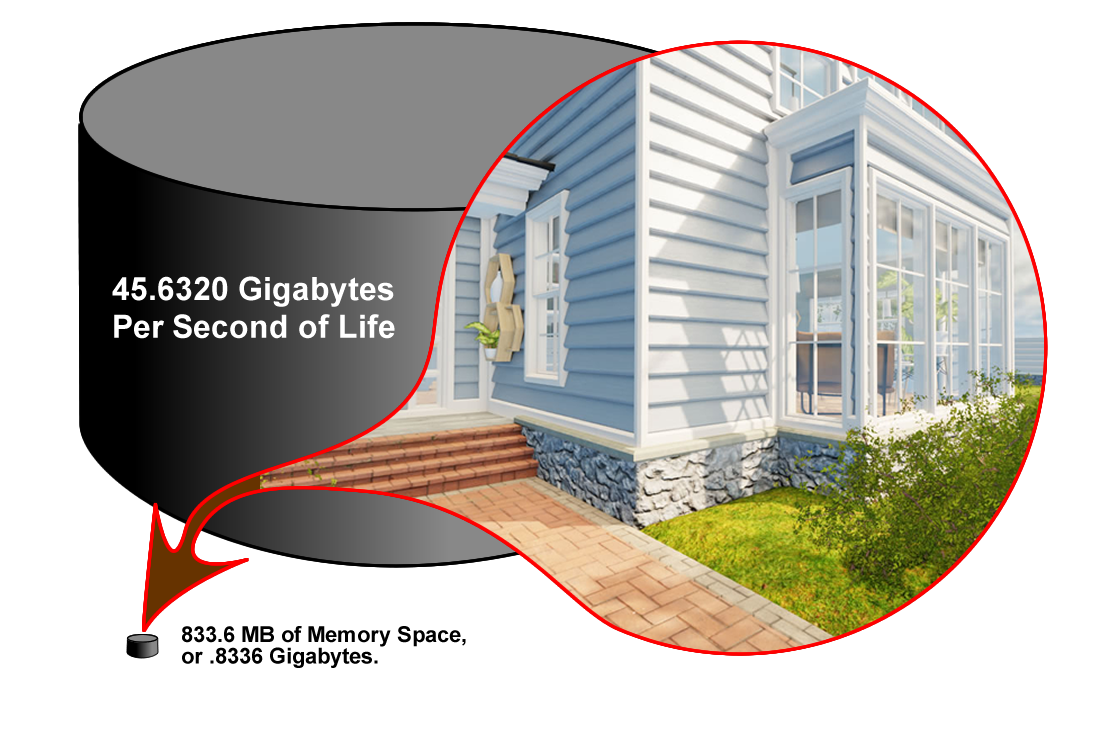
The diagram shows the memory required to store a fully developed environment of a house. The implication is that this 3D model memory requirement is about the same size as storing a moment of reality. The result is 45 gigabytes. A 64-bit computer can store 17 billion gigabytes.
• This three-dimensional environment model requires 833.6 MB of memory space, or .8336 Gigabytes.
In conclusion, you could store 50 models like this for every second of life for 100 years and still have memory left over. So yes, if you look at it this way, 64-bit memory is large enough to store a lifetime in its entirety. It seems to be eminently doable.
6.6. Conclusion: Proving Afterlife Using Information
In the tapestry of human existence, all environments encountered during a lifetime do reside in memory, intimately interwoven with our being. A lifetime of experiences, perfect in every way, accompanies us perpetually. As life's journey nears its end, the repository of memories stands with us. Within this treasure, all past environments exist. We will be exposed to our human voyage through the years.
Memory can be thought of as a physical time/space continuum [Postulate 4]. At the end of life, it will unveil itself as an ethereal universe. It will be filled with the myriad tapestries of human interaction. People, emotions, and reflections of profound thoughts - the very essence of love, compassion, and all that adorns humanity - exist within this vast four-dimensional domain.
Such a sight will unfold before our eyes: a boundless expanse, extending beyond the temporal horizons, bearing witness to perpetual existence. Within this realm lies an accumulation of realities, waiting in eager anticipation to be perceived and understood. A storehouse of potentialities, unrestricted and immeasurable, stands poised for realization - a manifestation of the universe.
As we approach our conclusion, we find ourselves in the presence of an unparalleled opportunity. We are finally able to seize these untapped treasures of cognition, to unravel the veil of the unknown as if a privilege is bestowed upon us. We now embark upon an epoch-making expansion, charting new trajectories across the limits of the universe. Let us, then embrace the vast realm of memory. We can see in the diagram below that when the power is turned off, we are embraced by all memory. Afterlife need not be more than one moment in duration because within that one moment is infinite time itself.

This diagram shows that total memory begins at the moment life begins, retains everything during life, the ends the moment life turns off. The results is a four-dimensional (4D) time-space continuum.
During life's tenure, conscious awareness dwells at home in the present moment - the rightmost corner of this diagram above. However, upon seeing the realm of the afterlife, a profound transformation unfolds. Conscious awareness expands unbounded in all dimensions - embracing length, width, depth, and time. It transcends its former confinement from a mere point at the right side and manifests ubiquitously. It permeates the vast expanse of memory, embracing all epochs and every corner of the cosmos.
This metamorphosis is nothing short of astounding - the creation of time and space without bounds. Awareness becomes everything and assumes the size of memory. In its embrace, all information, all experiences, and all knowledge are realized. The very essence of the afterlife unfolds like a celestial orchestra, resonating with the grand symphony of memory.
During life, our awareness is akin to that of a central processor, limited in its scope to comprehension of the data in its handful of registers only. But at life's culmination, awareness transcends its former limitations, becoming aware of the vast unbounded reservoir of memory. This expansion can be visualized as a cosmic expanse - an event horizon akin to the genesis of the universe - the grand Big Bang that engenders the birth of enlightenment. This expansion, in its sheer magnitude, is prodigious beyond measure.
Consider, for example, the analogy of a 64-bit computer. In the afterlife, awareness grows exponentially, unveiling an inconceivable 18,446,744,073,709,551,616 (2 to the 64th power) times more information than resides inside the processor's registers. Such a staggering order of magnitude offers a glimpse into the enormity of the metamorphosis - the ineffable vastness that accompanies the expansion of awareness throughout the dimensions of time and space.
As awareness expands unbounded, we unearth the mysteries that were concealed within the tapestry of our former existence. We witness the ever-unfolding grandeur of creation. In the afterlife, conscious awareness transforms into the wonders that abound within the infinite cosmos of time and space.
-- This Concludes Proof Of Afterlife By Information --